Zero Trust cloud security to prevent ransomware attacks

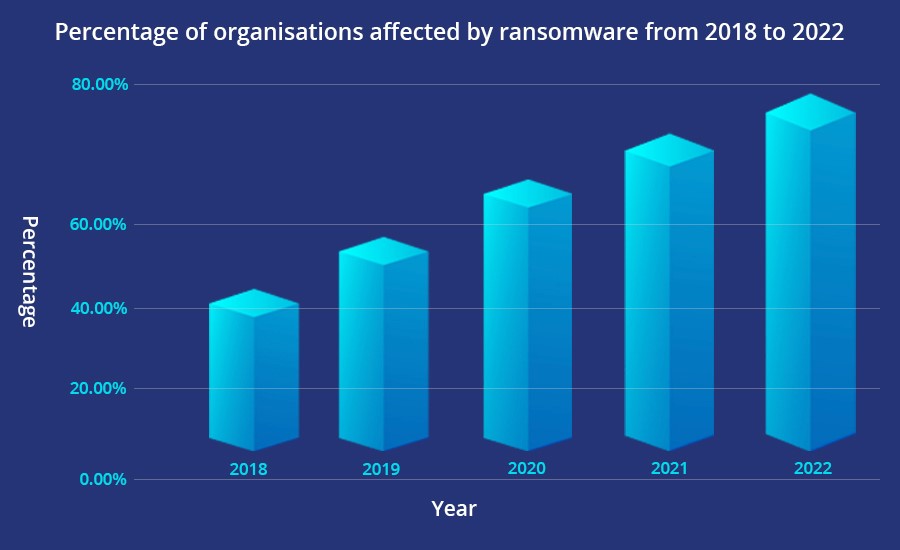
In the recent few years, ransomware in cyber security has turned out to be an extremely hot topic. More importantly, companies are finding it difficult to face the aftermath of a ransomware attack because the overall cost of recovery has increased significantly. Every day, there are 4,000 ransomware assaults globally. As per research conducted by Cybersecurity Ventures, by the year 2031, the cost of ransomware will probably surpass more than $265 billion dollars in total. With the increasing use of cloud computing and the associated vulnerabilities, many organizations have started to look for ransomware protection to protect their cloud data and applications.
One of the most effective security solutions is through cloud-managed and support services ; Zero Trust Cloud Security, a framework that requires organizations to closely monitor and restrict access to their cloud services. This proactive approach can help prevent ransomware attacks, which are becoming more prevalent and sophisticated by the day.
In this article, we will discuss ransomware attacks and how Zero Trust Cloud Security can help prevent ransomware attacks and assist companies in protecting their data and information from the same.
What Is Ransomware in Cyber Security?
Ransomware attacks are a form of cyber-attack in which malicious actors encrypt data on a system, often making it unavailable until a ransom is paid. These attacks have become increasingly popular in recent years due to their effectiveness and the low risk for attackers when they complete the ransomware removal after receiving their money.
The entire process of a ransomware attack is extremely simple, which we have explained using three steps:
- The attacker infects their targeted system with malware and successfully encrypts all the important information and data the company has stored.
- Then the attacker sends an email to the victim company or organization stating that they need to purchase the information by paying a ransom amount.
- After the ransom has been paid, the attacker may enable the company to access their data.
Ransomware attacks can cause significant financial losses and reputational damage for organizations, making it essential to implement effective cloud security measures and ransomware protection to prevent them.
Zero Trust Cloud Security as The Solution of Ransomware Attacks
Businesses must take the right protection precautions to keep their security teams from becoming attack fatigued. One of the most effective security solutions for these kinds of security threats is Zero Trust Cloud Security, a framework that requires organizations to closely monitor and restrict access to their cloud services. This proactive approach can help prevent ransomware attacks, which are becoming more prevalent and sophisticated by the day.
What is Zero Trust Cloud Security?
Zero Trust cloud security is an effective way to protect against ransomware attacks. This framework requires organizations to closely monitor and restrict access to their cloud services through cloud support and managed services. By doing this, organizations can ensure that only authorized users can access the data and applications within the cloud environment.
If your company or organization is currently using traditional network security the chances are that you will not be able to receive ransomware protection because attackers can easily get into your system and move freely across internal systems with no opposition.
On the contrary, Zero Trust Cloud Security is a security system that views everyone and everything as hostile. The first person to use this ‘Zero Trust’ phrase was an analyst named John Kindervag. The Zero Trust Cloud Security is based on the concept that everything should always be verified, and nothing should ever be taken at face value. Zero Trust Cloud Security does not consider whether a person is inside the network perimeter or outside. It will strictly check each person as well as devices before giving them any access or permission. Therefore, identification is the prime factor here.
What Are the Core Principles of The Zero Trust Framework?
If you think that Zero Trust Cloud Security is a straightforward technology, then you would be in the wrong because it encompasses more than one technological solution or approach. You can create an entire ecosystem with the help of Zero Trust Cloud Security that will prevent any kind of ransomware in cyber security. Let us look at the core principles of Zero Trust Cloud Security.
Micro-Segmentation
In micro-segmentation, the security perimeters are divided into smaller zones which enables the company to manage the access of different parts of the network separately. Therefore, anyone with access to a particular zone will not be able to access another zone (if they don’t have proper authorization).
By any chance, if attackers gain access to your network or system, they will not be able to move freely because micro-segmentation will potentially restrict their movements and access to the entire network. Since each network section needs a separate authorisation, this greatly reduces the attack surface.
Least privilege principle
The least privilege principle is another component that makes Zero Trust Cloud Security unique. Here the user or device will receive the least amount of access which means you will only be able to perform limited work or operations with this.
When giving access to individuals or programmes, network administrators must exercise caution and ensure the withdrawal of such rights when they are no longer required. With the help of the least privilege principle, the explosion radius can be decreased exponentially and limit a user's access to delicate network areas.
Frequent verification
Zero Trust Cloud Security is currently being accepted by a lot of companies and organizations because of the robust security it provides through frequent verification processes. In a Zero Trust Security model, it is already expected that attacks can come from both inside and outside, therefore, not a single entity or device should receive total access to confidential information and apps.
The integrity, rights, and origins of the users and machines are continually verified by this approach. That is why a lot of times users are forced to re-verify their credentials when a connection timeout occurs.
Endpoint Security
Along with least privilege access Zero Trust Cloud Security also takes care of the security of the end-user and safeguards them from any security risk. Each and every end-user as well as their devices are constantly checked for malware, network access and malicious behaviours so that both the network and system do not get jeopardized.
Benefits of using a Zero Trust Cloud Security
There are several issues with the conventional security model that can be addressed by zero-trust. Let us have a look at the benefits you will receive along with ransomware protection by implementing the Zero Trust Cloud Security model:
Decreases the threat of data leaking
As mentioned earlier, Zero Trust Cloud Security operates through micro-segmentation which means every part of the system is divided into smaller segments in this network. A user will have limited access and that is why there won’t be any threat of sensitive data leaking from the system or network.
Protects you from potential data loss
The occurrence of data breaches is exponentially increasing, and companies have to suffer major financial losses due to the same reason. Henceforth, by implementing Zero Trust Cloud Security you will be able to protect your company from expensive data breaches as well as receive ransomware protection
Protect your system from both internal and external hazards
Zero Trust Cloud Security considers every user as well as device as malicious. Therefore, if a threat is coming from the outside or inside of the system, detecting them will be a piece of cake for Zero Trust Cloud Security.
Enables proper security measures for the remote workforce
Due to drastic technological developments, it has now become possible to work remotely which means the employees of an organization can access its system with valid credentials from anywhere in the world at any time. Maintaining the security of this dispersed workforce has been made possible by endpoint security solutions offered by Zero Trust Cloud Security.
With the drastic increase in ransomware attacks, it is already proven that if a company wants to protect their data against these attackers, then it will have to implement the Zero Trust Cloud Security Model. With the support of Zero Trust Cloud Security and cloud support and managed services, companies and organizations can enjoy better security features which also can manage remote work culture as well as a widespread workforce. The attack surface area can be significantly reduced because of the least privilege access principle and network segmentation applied by the Zero Trust Cloud Security. The principal tenet of Zero Trust Cloud Security remains that no single user or device should ever be trusted and that everyone must be verified before being given access to resources. By implementing this your company’s security system will become robust which will ultimately lower your risk factor and offer you ransomware protection.
CloudIBN provides complete Azure services, including the implementation of Zero Trust Cloud Security, to ensure your data remains secure. Our expertise in deploying Microsoft's advanced security measures allows businesses to protect their data, manage remote workforces, and reduce risks. Partner with CloudIBN to enhance your cloud security and enjoy peace of mind. Visit us at www.cloudibn.com or contact us at 020-711-79586 to learn more about our Azure services and how we can help secure your business against ransomware attacks.